In 2017 a US ally shot down a $200 drone with a $3 million Patriot missile. Clearly this is overkill, but it gives an idea about the challenges security is facing and how a drone you can find in a civilian market can pose a threat for military forces.
Since then, we started to develop counter-drones systems trying to detect them and eventually jamming the frequencies they use to receive commands, but we can still develop nanodrones, drones smaller than the usual employed for open field actions that can communicate on scattered frequencies.
These kind of drones are hard to detect and hard to neutralise… and David Meléndez Cano explained how to build one of them at Codemotion Rome 2019.
Nowadays, drones are employed for many tasks from wedding days to surveillance. For this reason, the regulation to have and pilot a drone is becoming stricter everyday.
One of the reasons for a specific regulation is the possibility of using drones in battlefields and their consequent threat to the current state-of-the-art equipment of military forces. Actually, General David Perkins, the commander of the US Army Training and Doctrine Command (TRADOC), spoke at the Association of the US Army’s Global Force symposium, where he discussed the threats that the US military would begin to face in the coming years. One notable example is how a US ally recently shot down a $200 consumer drone with a Patriot missile.
Perkins’s talk during the symposium focused on the complexity of a military organisation in the field and how the interconnected nature of air, ground and sea forces can lead to a fragmented response to a threat between the commanders who are in charge of specific areas. He specifically spoke about the necessity for commanders to address threats holistically. He used one specific example of how this occurs on the battlefield: hostile, civilian Unmanned Aerial Systems (UASs).
“In fact,” he went on to say, “we have a very close ally of ours that was dealing with a adversary using small quadcopter UASs, and they shot it down with a Patriot missile.” The problem, he said, wasn’t effectiveness —the tiny drone didn’t stand a chance — the issue is economics. The situation showed that whoever was flying the drone knows that they can easily undermine this unnamed ally with the missiles. All they need to do is buy more cheap drones and fly them, running up the operational costs of that military. As Perkins notes, using a $3.4 million missile to destroy a civilian drone is enormous overkill.
Counter-drone systems
Actually drones can be considered as flying computers and they can carry sniffers, jammers, network analysers, cameras, explosives, etc.
For these reasons, over the years, counter-drones systems have been developed with the specific aim to detect and neutralise drones.
This kind of systems use different approach for detection:
- standard cameras to detect the shape of drones approaching
- electronics and motor heat detection with thermal cameras
- characterisation of drone noise
- detection of radio frequency and waveform related with the communication between the drone and the pilot control. In fact is possible to identify a radio signature for this kind of communications.
When detected, you can take down a drone by jamming its communications and actually this is the solution often adopted to create a “quiet zone”. Be aware anyway that in many countries this is an illegal practice, since the use of jamming devices can place people in danger. For instance, jammers can prevent emergency calls from getting through or interfere with law enforcement communications (ambulance, fire, police, etc). In order to protect the public and ensure access to emergency and other communications services without interference, the use, marketing, manufacture and sale of jammers is mainly prohibited.
A different approach to prevent the threatening use of drones comes under the name of “voluntary measures”, like installing a chip on any drone that has the power to take control of the UAS when police or governative forces require. For sure this is not something easy to accept and it sounds like giving up freedom to be more secure.
For these reasons, we can say that at the moment we can easily detect drones, but there is not yet a solution about how to neutralise them out of a military context.
Counter-Countermeasures and the project
Nevertheless, suppose we are facing a counter-drone system, how can we avoid it?
David gives us the answer, proposing different solutions:
- spread-spectrum: the possibility of spreading the communications in a frequency band so that the intensity of the signal for a specific frequency can be easily confused with noise and the signal is not detected;
- frequency hopping: the possibility of jumping from one frequency to another during the communication, avoiding jammers which confuse the signal on a specific carrier;
- use unexpected frequencies by the jammer: the decision to work from communications within a non-standard operational band;
- Robust protocols: adoption of robust protocols for communications.
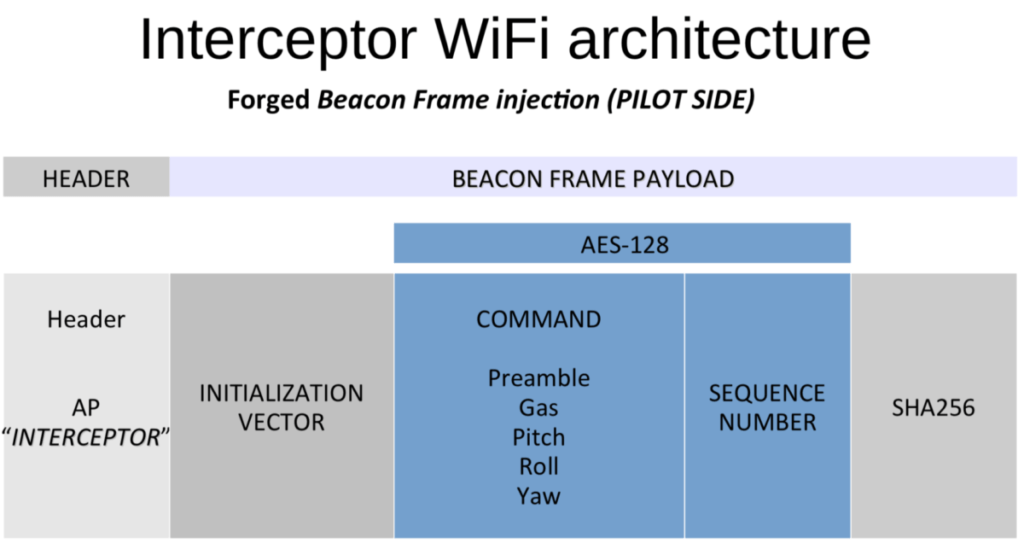
Here comes “The Interceptor” project, a quadcopter drone that should have a minimum size and weight (that means it is hard to detect with a standard or thermal camera), low budget, hacking capabilities and resilient control.

Here comes the trouble since not all the four channels are available for the PWM ports since two of them are shared with UART2 ports and, by default, Vocore2 comes with the UART2 enabled and the two PWM disabled.
To do that, you will need to download the source code and hack the configuration checking out the pin schema.
When you have your motors controlled by PWM, you will need to tune them to have a smooth control of the drone and finally set up a resilient communication like the one in the figure.