Bruno vs Postman Bruno is an open-source API Client that has been gaining traction, challenging the highly popular Postman. This project aims to grow with community support, without third-party company involvement (except as sponsors) and has a … Read more
Backend
The Backend Developer is a programmer who creates the logical back-end and core computational logic of a website, software or information system. The main activities usually concern the three functional aspects of the back-end:
Programming: he has the knowledge of different programming languages like Java, JavaScript (NodeJS), PHP and the knowledge of methodologies and Frameworks such as Spring and
Hibernate. It is also able to work on more structured languages such as Ruby and Python.
Database Designing: a Back-end Developer has expertise in database management such as Oracle, MySQL or MongoDB.
Web Tool: is essential to be familiar with SOAP (Simple Object Access Protocol) and REST (Representational State Transfer) for integration with different infrastructures.
Open Source: The Awakening of PgSQL
Introduction In the era of vector databases, AI, and cloud computing, traditional SQL may seem outdated, but this is far from true. PostgreSQL, a resilient open-source database, has emerged as a strong contender in 2024, revitalizing the use of … Read more
Bridging Systems: Tackling the Complexity of Cross-Domain Interoperability
Introduction In today’s tech-heavy world, blending different technologies to work seamlessly together is crucial. That’s where Cross-Domain Interoperability (CDI) steals the spotlight—it’s essential for any forward-thinking business and a crucial … Read more
The Importance of User Management for Your Applications: Technologies and Best Practices
What Is User Management? User management refers to the processes and methodologies employed to control who has access to an application or system. It includes tasks such as creating user accounts, assigning roles and permissions, managing … Read more
OramaSearch: Your New Favorite Search Engine
What Is OramaSearch Welcome to OpenDev Explorer, where I explore the Open Source world with an eye on developer experience. I am Riccardo (aka TheZal), and today I will talk to you about OramaSearch, an open-source search engine with a "battery … Read more
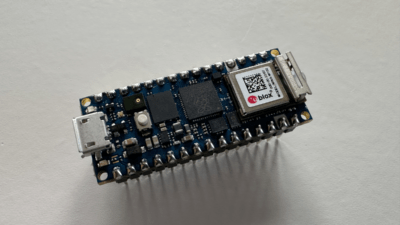
Getting Started With MicroPython on Arduino Nano RP2040 Connect
Although embedded systems have existed for several decades, only in recent times have they evolved into user-friendly technologies accessible to hobbyists without specialized knowledge. With the advent of new microcontroller architectural designs and … Read more
Project Idx: A Visual Studio Code Competitor
Visual Studio Code (VS Code) by Microsoft has stood out as one of the most beloved and widely used code editors globally. With its intuitive user interface, extensive range of extensions, and support for multiple programming languages, VS Code has … Read more
Code Mapping: How It Works and 5 Compelling Use Cases
Table of contentsWhat Is Code Mapping?How Code Maps WorkCompelling Use Cases of Code Mapping1. Debugging Complex Systems2. Refactoring and Code Optimization3. Onboarding New Developers4. Integration of Software Modules5. Documentation and Knowledge … Read more
The Ultimate Code Review Checklist for Developers
As developers, every line of code we write counts towards forming the backbone of our applications. Yet, being human, any line of code we write could contain bugs that cause problems for our customers and our teams. This is where code reviews come … Read more
Distributed Cache: How to Boost System Responsiveness
Distributed cache can improve the responsiveness of today's high-performance web and mobile apps. At heart it's a simple concept, but, when used well, it can bring improved capacity and flexibility to networked systems. As well as classic caching … Read more
How to Guide: Asynchronous Batching for Stampede Prevention
A cache stampede can occur when web servers face very high loads. To maintain the efficiency of backend services, caching is vital. But if the caching mechanism comes under intense strain, slow performance and even failure can occur. While there are … Read more
What Are Microservices Design Patterns?
Looking to get started with microservices design patterns? First things first: microservice architecture is an organizational approach to software development where the programmer has to use a collection of small autonomous services. These services … Read more
Black Friday: How to Manage Huge Traffic on Your App
It's a known issue both for users and developers: the extra traffic during Black Friday and Cyber Monday can cause e-commerce and payment apps to crash, generating many problems such as bad user experience, faulty transactions, revenue loss due to … Read more
10 Commonly Used SQL Commands For Solid Databases
Structured Query Language (SQL) databases have a long history of reliability. That’s why, despite being invented in the 1970s, they are still in use today. By inputting SQL commands, a user can gain instant access to data records. Over the … Read more
How to Easily Migrate from Spring Boot to Micronaut
In the beginning there was only JVM The JVM (Java Virtual Machine) is a virtual machine that acts as a runtime engine for running java applications and programs and programs in other languages compiled by Java bytecode. It has two main functions: … Read more
Fast Document Similarity in Python (MinHashLSH)
Why is document similarity more important than ever? In the big data era, it is always more frequent that companies need to detect similar items in their database. Imagine platforms like Kijiji or Subito, trying to detect people that constantly … Read more
This is Why The Future of Programming Is Composable
Let's start with the basics of composable programming and why it's such a big thing in software development. The "bible" of composability states that the best way to build an app is to write code once, deploy many times, stack, and expand … Read more
How to Deploy a Subnet on Avalanche Blockchain: The Case of DeFi Kingdom
What Is Avalanche Avalanche is an open-source platform for developing decentralized applications and enterprise blockchain deployments in a highly scalable, interoperable environment. It is the world's first decentralized innovative contract … Read more
Generating a Kubernetes Manifest with Dekorate the Easy Way
Why use Dekorate for a Kubernetes manifest? Well, the practice of deploying applications has seen a lot of changes in the relatively short time that computer systems have been part of our daily lives and business operations. One of the latest … Read more
What is Web3 and What New Capabilities Does it Bring?
What exactly is Web3? The term Web3 is used to refer to the Internet’s next stage, which will in theory be characterised by being a decentralised online ecosystem. The idea is that within this ecosystem, users will be owners and therefore will not … Read more