Web security is a topic that just won’t go away. Every day we hear the latest revelations – look at the latest scandal with Marriott admitting over 500 million customer records have been stolen using a breach that had been active since 2014!
Dave Lewis, a CISO at Duo, now part of Cisco, has over 15 years’ experience in the security business. As he says, he’s seen it all, and has learnt from his own mistakes. But he is depressed to see companies make the same mistakes time and again.
Injection
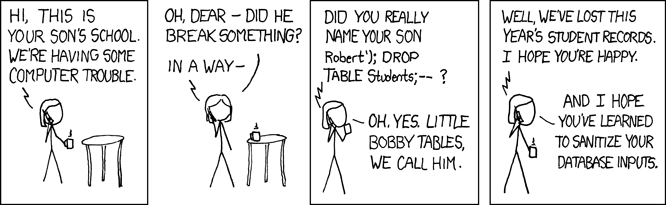
Injection attacks have been around since forever, yet they still cause issues. In particular, SQL injection attacks are often all too easy as highlighted in an early XKCD cartoon.
XSS
Cross site scripting allows attackers to do bad things to your site, from interface changes and code injection to hijacking and redirecting traffic. There are three classes of XSS attack. Reflected attacks allow attackers to do things like bring up their own popups; Stored attacks are where attackers store their script somewhere on your server; DOM attacks modify the local environment in the browser. All these attacks have been known about for years and protecting against them is relatively straightforward. For instance, using content security policies and frameworks such as Ruby on Rails which solve almost all XSS vulnerabilities.
Configuration
Often vulnerabilities are caused by misconfigurations or plain lack of common sense. As an example, Dave told us about a (nameless) Canadian company he was working for. On one page he found hidden in the comments “User admin; password admin”. Lo and behold, when he entered these they were indeed the admin credentials for the whole site. Clearly, they had been put in the source during development, but no one had thought to edit the source post-release, or to update the password.
Authentication
In Dave’s views, passwords have long-since passed the end of their useful life. All of us reuse passwords across multiple services and many people use plain dumb passwords. The problem is that a password just proves that you have the password, not that you are authorized to have and use it. The solution is multi-factor authentication and a move away from dumb passwords. Fortunately, as of April this year, WebAuthn has been adopted as a standard, which should help make this easier.
Broken Access
One of the worst sins is to fail to secure your site properly. A couple of years back, Dave was dealing with a series of attacks by the so-called Lizard Squad. Unbelievably he found that they had failed to secure their own site with a .htaccess file. As a result, he was able to find details of all the members and was able to shut down the attacks. Open ports are another easy attack vector to deal with – on the day of the conference, Dave found over 34 million vulnerable open ports across Germany, 1.9 million of them in Berlin.
Known Bad
Known Bad is a serious problem for many companies. To remain secure, it’s essential to keep your software updated against known attacks such as Heartbleed. Dave pointed us to a few useful tools including synk.io and wpscan.org. He also suggested it may be worth testing your own site using pyfiscan, a tool included in Kali Linux (a version of Linux for pen testing).
Logging (or its lack)
The final deadly sin is poor logging. The fight against hackers is never-ending, and fundamental vulnerabilities like Spectre and Meltdown keep being found. So, even with the best security you may find yourself vulnerable. This means it is essential to make sure you log everything you can. Then when you have a problem at least you can track it back properly.